How do I setup the Windows User for wmic (or what permissions do I need)?
The Easy (Insecure) Way
Add a new user and add them to the administrators group. Perhaps disable login privileges. Possibly suitable for test environments etc.
A Better Way
Scroll about halfway down this page to the section titled “Configure remote WMI access in Windows”.
**Note that some people report that even after following the above instructions that not all checks work. We have not yet determined a resolution for this problem. Most of the time using an administrators account fixes this problem. If using the administrator account fixes your errors then you almost certainly have a permissions problem.
This page may also be helpful.
The primary relevant content from the op5 site is also available here
Other Permissions Snippets
There have been many suggestions scattered around the Internet on how to setup the permissions for wmic access. Some of them have been reproduced here. Its typically going to come down to try various combinations and see what works for you.
WMI Connection Testing
This standalone executable sometimes gives somewhat more useful error messages to help find the WMI connection/permission issues:
Windows Management Infrastructure
- (Start → Run …) wmimgmt.msc
- Right-click on WMI Control (Local) Properties →
- Security
- → Root CIMV2
- Security
- Add users with the privileges:
- Enable Account
- Remote Enable
Enabling Remote DCOM
- Add the user (s) in question to the Performance Monitor Users group
- Under Services and Applications, bring up the Properties dialog of WMI Control. In the Security tab, highlight the root / CIMV2, click Security; add Performance Monitor Users and enable the options: Enable Account and Remote Enable
- Run dcomcnfg. At Component Services> Computers> My Computer, in the COM Security tab of the Properties dialog click “Edit Limits” for Both Access Permissions and Launch and Activation Permissions. Add Performance Monitor Users and allow remote access, remote launch, and remote activation
- Select Windows Management Instrumentation under Component Services> Computers> My Computer> DCOM Config and give Remote Launch and Remote Activation privileges to performance Users Group.
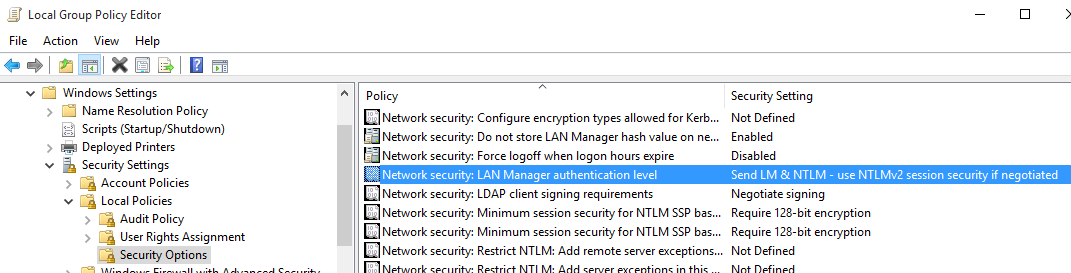
Allowing NTLM
Run gpedit.msc and configure the following setting:
Forcing NTLMv2
Add the following command line argument to Check WMI Plus to force the use of NTLMv2:
–extrawmicarg “–option=client ntlmv2 auth=Yes”
Make Sure the Account is Active
Using an administrative command prompt
net user USERNAME /active:yes
Windows Firewall
Make sure the Windows firewall will allow wmi connections from the Check WMI Plus client.
If you are not sure if you have a firewall issue, disable the firewall and test. If it works when you disable the firewall but not when the firewall is enabled, then you need to add the correct firewall rule.
Workgroup and Systems that cannot communicate with their Domain
There are some reports that you have to disable UAC if you’re checking against a system that’s either in a workgroup or cannot communicate to a domain (even if joined).